The Role of Physical Security in IoT
Physical security, also known as silicon or hardware security, involves securing the silicon element of a system. This blog explores the different physical attacks and Arm IP on offer as a counter-measure.
Securing the Internet of Things (IoT) continues to become more important as the value of assets, and number of connected devices, continues to increase. The distributed and fragmented nature of IoT means a larger attack surface and physical access (proximity) to the devices. The combination of these two factors make physical security a viable and potent threat. There are many examples of how a lack of sufficient physical security can pose a severe security risk to the IoT ecosystem and the effects of a security breach can quickly snowball. For example, a system that uses fingerprint authentication for identity access. First the hacker overcomes authentication which provides access to personal data, access to credit card information and more, and once one device has been hacked, the hack is applied remotely enabling access to thousands of devices.
Arm has identified four types of vulnerability that should be considered when designing a system-on-chip (SoC); software, communication, lifecycle and physical. If one of these vulnerabilities isn't protected, the whole system becomes compromised, so it is important to ensure all necessary mitigation measures are considered and implemented at the very beginning. A range of counter-measures are recommended to ensure that all attack opportunities are mitigated.
Physical security, also known as silicon or hardware security, involves securing the silicon element of a system. A key, notable difference from software security is the proximity to the device. Software attacks can be carried out remotely, while physical attacks require close proximity. Below we will explore physical security in more detail and explain its role in securing the IoT.
What is physical security?
To understand physical security, it's worth looking at how it can compromise the IoT ecosystem. Consider the scenario where an IoT deployment, such as connected street lights, use AES encryption to deliver firmware updates. The intention is to make sure only authorized sources (who can prove the knowledge of AES secret keys) can deliver the updates in a secure manner. Now, an adversary can steal these AES credentials using Side Channel Analysis (SCA) and can later use these stolen keys to hijack the streetlight network. This attack has been demonstrated in real life. The attacker needs to be within the proximity of the device to carry out the attack and gather the sensitive information. There will be no remnants of the SCA attack afterwards. The consequences of such hacks can be even more severe when an attacker can use SCA to compromise the security of bank cards, mobile devices, or even medical devices.
There are two types of physical vulnerability, non-invasive and invasive.
- Non-invasive attacks require the attacker to be close enough to target the chip and sense electrical characteristics, this allows the attackers to change the behavior of the devices or gather sensitive information
- Invasive attacks need the chip surface to be exposed, meaning that the chip can be physically manipulated
Within these two categories, there are also a number of different types of attacks, shown in the image below.
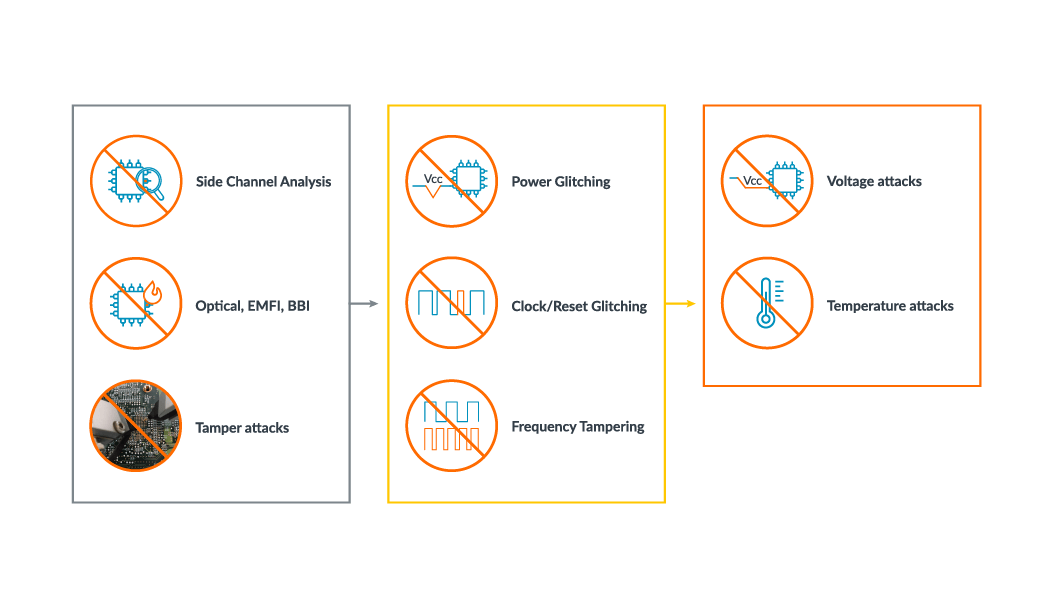
Fig. 1: Physical security - range of threats to be mitigated
Side channel analysis is a non-invasive attack which involves an attacker analyzing power signature or Electro Magnetic radiation emanating from an IC with the aim of extracting sensitive information such as secret keys.
tamper attack is an invasive attack where an adversary will physically tamper the IC with the objective of gathering sensitive information present in the metal wires using micro probes. An adversary might even try to alter the circuit behavior by overdriving the state of the IC.
Fault injection attacks or Perturbation attacks occur when an adversary induces a faulty behavior in a system with the intention of taking advantage of these faults to compromise the security. there are several methods to induce faults. some of the prominent ones are discussed below. Fault injection attacks can be both invasive and non-invasive in nature.
Optical, ElectroMagnetic Fault Injection (EMFI), Body Bias Injection (BBI) are types of perturbation attacks that aim to inject faults into a device by means of projecting lasers, Electro Magnetic fault injection and biasing the body. An adversary will try to exploit the faulty behavior to compromise the security of the system.
Power/Clock/Reset glitching attacks occur when an adversary tries to introduce glitches in the power supply, clock network or the Rest network of an IC. The objective go an attacker in this case is to induce faulty behavior that can be exploited to compromise the security.
Frequency/Voltage tampering are attacks in which an adversary will change the operating conditions of an IC. They can try to tamper the level of power supply, or change the clock frequency of an IC. The objective of the attacker in this case is to induce faulty behavior that can be exploited to compromise the security.
Temperature attacks involve an adversary changing the operating environment by changing the temperature of operation for an IC. The objective of an attacker in this case is to induce faulty behavior that can be exploited to compromise the security.
Why is physical security important?
As mentioned earlier, there are four different vulnerabilities which can be represented by different entrances to a house, see fig. 2 below.
Software vulnerabilities are represented by the door, they are easiest to attack and have specific counter-measures to protect devices from software attacks, locking the door. Lifecycle and communication attacks are represented by windows in the house, these are more difficult to attack and, again, have counter-measures to mitigate against these attacks and lock the windows.
Physical security is represented by the attic window, this is the highest entrance to the house, and therefore, the most challenging to reach. In the past, securing the attic window was hard to justify in terms of value. However, a number of factors have changed over time, increasing the importance of physical security. These include:
- Other vulnerabilities (or entries) being secure and more difficult to hack
- An ever-increasing network of connections with growing values of assets, providing greater opportunity to scale into a large-scale attack and therefore a higher incentive to attack
- Rise in opportunities to carry out physical attacks (represented by the ladder), a growing number of tools for the attacks, cheaper technology used to carry out attacks, and more accessible ways to attack, making it easier for anyone to attack
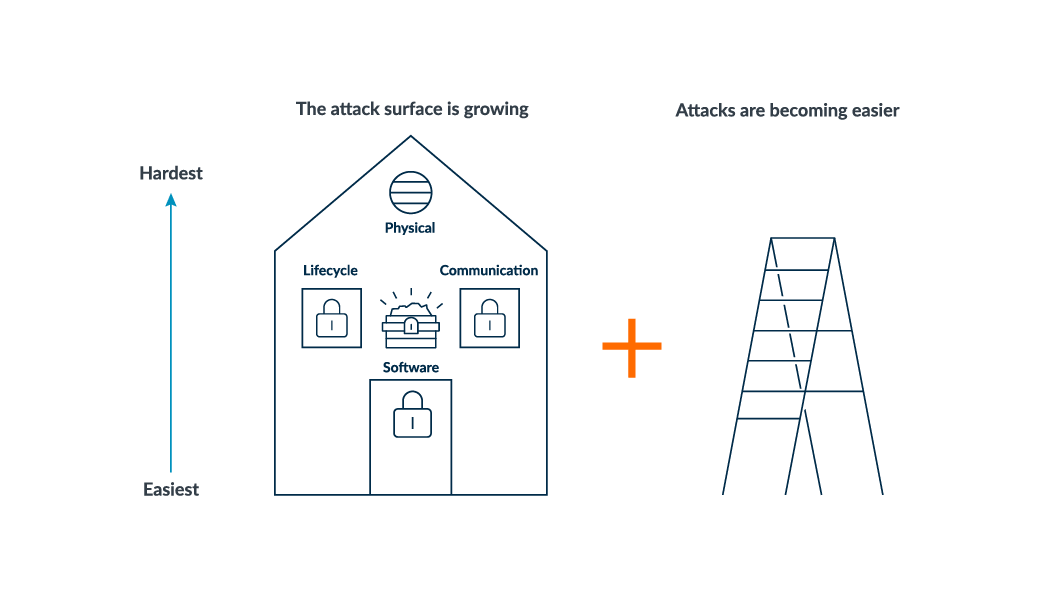
Fig. 2: Sophisticated attacks require higher levels of security
Sounds scary, is this a new threat?
Physical security is not a new concept - we've seen it before in our everyday lives, in credit card chips and in smartphone chips - the threats have been around for years. The risk is expanding though, with an increase in more accessible IoT devices with hold valuable information, are prone to physical interaction and provide benefits to hackers.
How can you protect your devices from physical attacks with Arm?
Arm provides a number of software and hardware-based counter-measures for physical attacks.
 |
 |
 |
| Cortex-M35P | CryptoIsland-300P | CryptoCell-312P |
| Arm Cortex-M35P adds physical resilience and system safety functions, such as lockstep, configurable parity, and observability, without compromising performance. Anti-tampering provides state-of-the-art security and prevents costly security breaches. Download this guide to learn more about the features and benefits of the Arm Cortex-M35P processor. | Arm CryptoIsland products isolate roots of trust and increase ease of reuse crucial to payment and identity applications. Arm CryptoIsland-300P combines physical isolation of the security subsystem. | Arm CryptoCell-312P is a comprehensive security solution for low-power, compact designs with features that protect the authenticity, integrity, and confidentiality of code and data belonging to different stakeholders. |
Software
Most software from a previous Arm-based SoC can be reused with little modification since the underlying physical security features will be hidden in hardware TrustZone software isolation requires the project to be split into a non-secure project that contains the RTOS, stack and user applications and a secure project that contains all the security assets such as secure boot, crypto functions, key storage and secure firmware update.
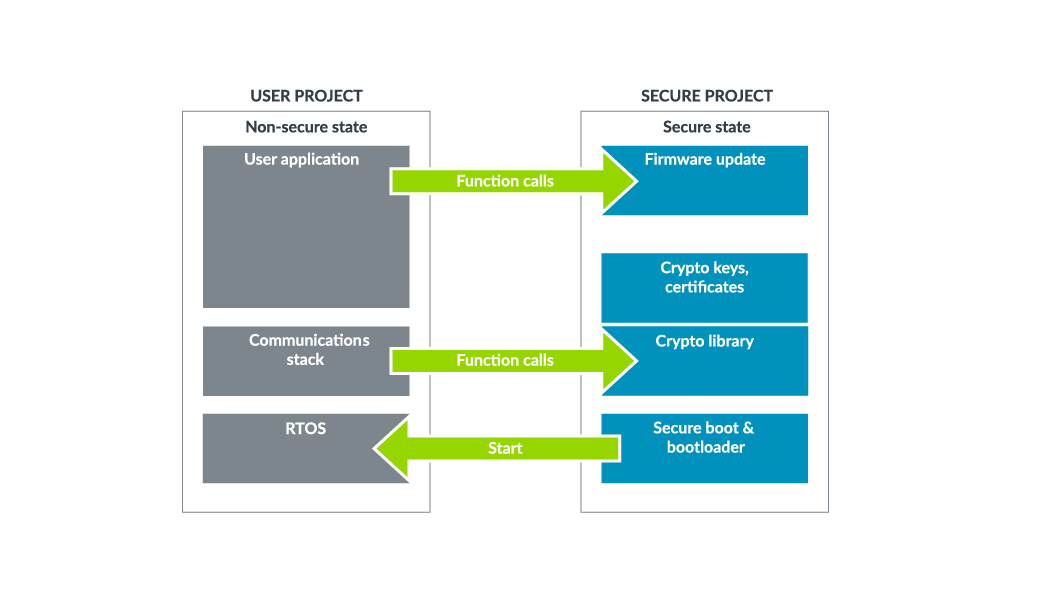
Fig. 3: Cortex-M35P with TrustZone software isolation
The bigger picture
Attacks can be catastrophic, and ensuring the right mitigation is built into the SoC from the start is paramount to lower the risk of attack.
Careful consideration needs to be made when deciding which counter-measures are implemented into a device. Depending upon various factors, including the threats and value of the assets, different vulnerabilities need to be identified and mitigated. The Arm Platform Security Architecture is a framework outlining common security standards that builds in security from the ground up through three key phases: Analyze, Architect and Implement. During the Analyse stage, Threat Modelling is carried out to consider the risks, threats and value of a device and identify which mitigation methods should be used. The identified counter-measures would then be designed in the Architect stage and built into the device at the Implement stage. PSA enables you to identify whether physical security is required in your design, and ensures that all entrances that need to be protected, are secure.
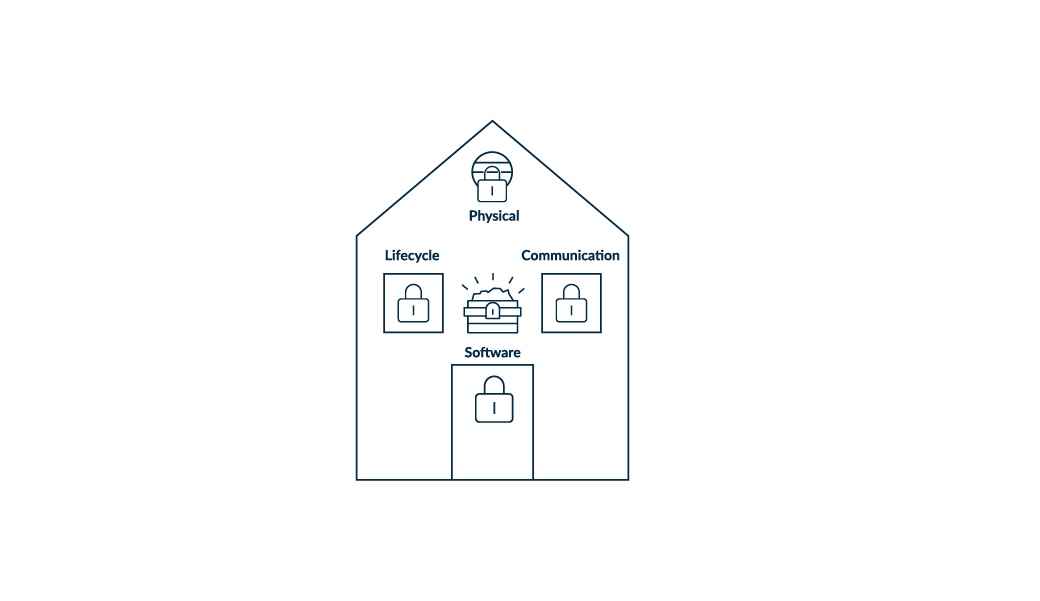 Fig. 4: Complete security solution, addressing all four vulnerabilities
Fig. 4: Complete security solution, addressing all four vulnerabilities
Arm provides the building blocks of IP to help SoC designers ensure security, in particular physical security, is built in from the ground up and integrated with all other security IP.
Re-use is only permitted for informational and non-commercial or personal use only.
