The IoT Architect's Practical Guide to Security
Follow a working example of IoT security using a smart door lock. Learn how the Platform Security Architecture (PSA) framework provides a practical way to design-in security to connected devices.
By Brian.

We understand the extraordinary potential of the Internet of Things (IoT), but how do we move from where we are now to a world of a trillion connected devices? To seize the opportunities within this market we must ensure the products that we are developing are future-proof and secure. Also, we need to build trust in emerging technologies and the data they provide.
The expectation and awareness of IoT security is at an all-time high and with this, new guidelines, regulations, and companies have emerged to guide requirements and best practices. While this all shows great progress in the industry, it can still be a confusing place to navigate. With all IoT products having unique security requirements, it is challenging to identify these requirements, and communicate security best practice across the ecosystem.
To provide clarity in IoT security, Arm and Cypress Semiconductor® have created an application guide detailed the process of designing security into an IoT device. This blog gives an overview of what you find in the full application guide.
The guide uses a smart door lock as a working example and details the security design for the Cypress PSoC® 64 line of Secure MCUs, which can be used as the platform for smart door lock implementation. While this focuses on a smart door lock, all the details are applicable to any IoT product, ensuring you protect your brand reputation and speed up security design.
Why we chose a smart door lock
We lock our doors to protect our most valuable possessions and to keep our loved ones safe. When we turn the key or fasten the latch, it helps us feel secure. So how do we ensure that digital solutions provide that same peace of mind?
Companies developing smart door locks are taking advantage of latest technologies to transform their businesses and people's lives. A smart lock replaces or bolsters a traditional security system. It enables you to open or close a door using a smartphone, key card, a PIN, or even your fingerprint. The smart door lock can keep track of who is entering or leaving a premises and alert you to unusual activity. However, this increased functionality can come at the cost of additional security vulnerabilities, so architecting trust into a smart door lock is critical.
The Platform Security Architecture: A simple, cost-effective security solution
Knowing what security is required and how to implement countermeasures can be complex and time-consuming. The Platform Security Architecture (PSA) was created to provide the tools that are needed to design and build security into IoT devices at scale. Documentation and specifications enable the right level of protection to be designed into products, saving time and reducing the cost of implementation.
A systematic framework for IoT security
PSA is a four-stage framework;
Analyze: assess the potential threats to your device and identify what you need to do to protect it.
Architect: create a system architecture capable of meeting your security requirements.
Implement: use a trusted code base, such as Trusted Firmware-M to implement the security requirements from the architect stage.
Certify: PSA Certified offers an independent testing and evaluation scheme for IoT chips, software, and devices that you can use to build and communicate trust with your customers.
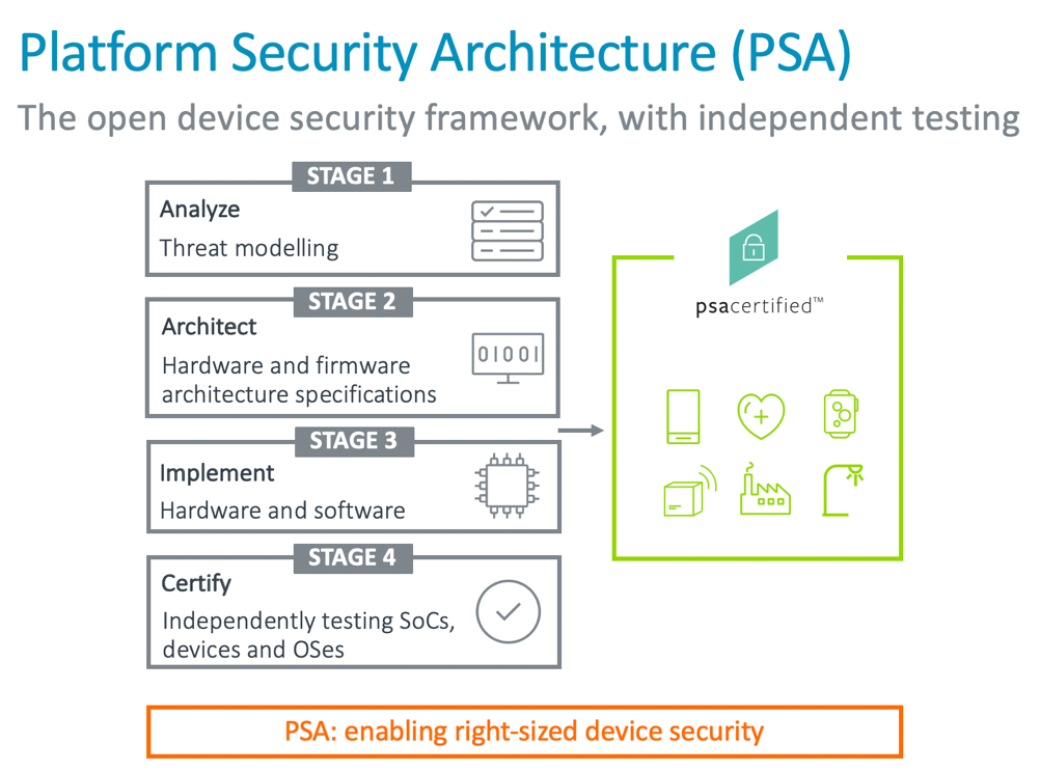 The Platform Security Architecture (PSA) provides a systematic framework for IoT security.
The Platform Security Architecture (PSA) provides a systematic framework for IoT security.
The PSA makes security more straightforward, even if you are not a security expert. It is aimed at different entities throughout the supply chain, from chip designers and device developers, to cloud and network infrastructure providers, and software vendors.
To find out more about the PSA and how you can create trusted IoT solutions, watch our on-demand webinar.
Applying PSA principles to a smart door lock
How do smart door locks work?
A typical smart door lock system is shown in the conceptual diagram below. Within this system, there will be assets, or components of your device, that are of value to you and your customers. They may include:
- Smart door lock device ID
- Firmware and its certificates
- Owner or guest credentials, including biometric data
- Audit logs
- Configuration and user data
- Network connectivity
- Biometric sensor, Bluetooth® Low Energy (BLE) and other hardware resources
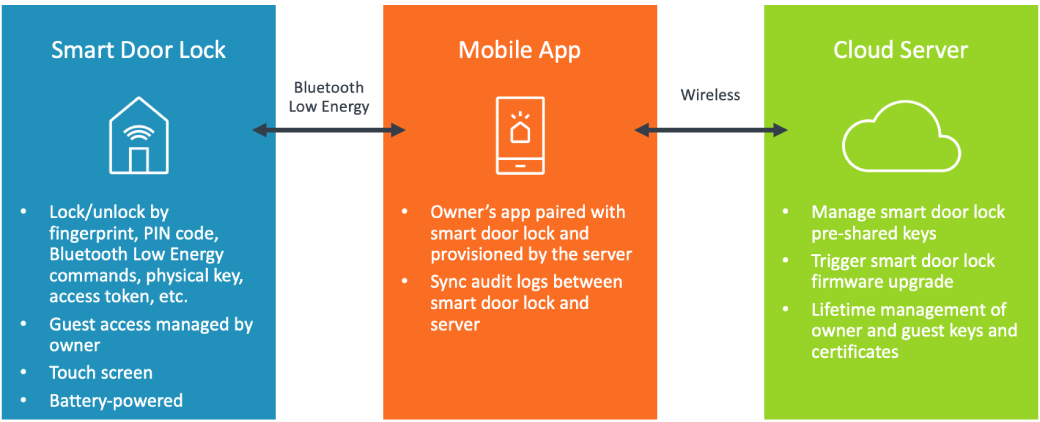
A typical smart door lock system.
Cyber-attackers target these assets in the same way as a burglar would search your home for an expensive watch, jewelry, or cash. In the case of a smart door lock, your digital assets may provide access to the physical ones. The question is, what are the weaknesses and how do you protect against them?
One attack example is an impersonator of a legitimate administrator, owner, or guest carrying out a malicious act. This attack could be countered through an authentication process - the device would authenticate the administrator before granting access to the lock configuration and logs, and before performing a firmware update, preventing impersonation.
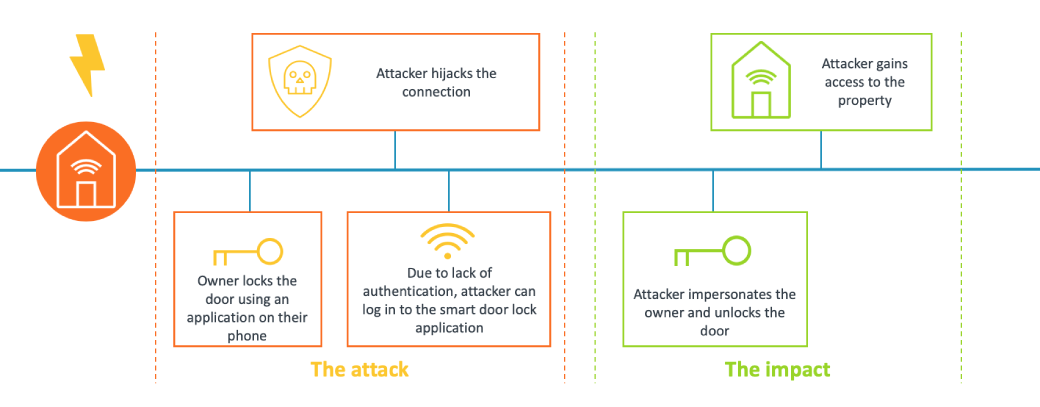
Example attack flow: A hacker impersonates the owner of the device and gains access to the property.
The exact requirements vary depending on the product. However, the cost and effort involved in securing a device and the investment an adversary is likely to make in carrying out an attack needs to be weighed up.
Follow the practical guide to IoT security design
The smart door lock application guide provides a practical guide walking through the four stages of PSA. Within this you will find:
- How to develop a threat model and security analysis document and derive security requirements and counter-measures from this
- A comprehensive explanation of the hardware architectures and security IP necessary to maintain asset security; from trusted boot to security hardware partitioning. Additionally, the use of PSA Firmware Framework to isolate and partition functionalities into Secure and Non-secure processing environments
- Details of how to access and use Trusted Firmware-M, the open source reference implementation of PSA, and the PSA APIs to isolate security critical functionalities from Non-secure code
- An overview of PSA Certified and how independent evaluation can provide assurance and a common foundation of security for the whole IoT ecosystem
For a real-life implementation of PSA for security design, download the Smart Door Lock Application Guide today.
Download the smart door lock application guide
Additional Resources
Find more information about the four stages of PSA on our website.
Start designing-in security by reading our blog on the first stage of PSA - Analyze.
Learn more about Cypress PSoC 64 Secure MCUs.
By Brian.
Re-use is only permitted for informational and non-commerical or personal use only.
